Do you want to have better protection against firmware hacks? Here’s good news. Microsoft reveals its “Secured-core PC” initiative. Come to this post, you will know more information about the “Secure-core PC” from MiniTool.
Why Microsoft Reveals Secured-core PC Initiative
There is no doubt that Microsoft puts more emphasis on the security of its Windows users. This initiative is planned to keep away some targeted firmware hacks.
As the ever-improving security features built into operating systems and their connected services, these firmware attacks become more and more common in recent years. Better security often brings more challenges for hackers.
However, a hacker can still break into a system by making use of various software vulnerabilities, which will lead to many firmware attacks. So, to address the growing firmware threats, Microsoft has cooperated with other PC manufacturing and chip partners to develop the Secure-core PC defense.
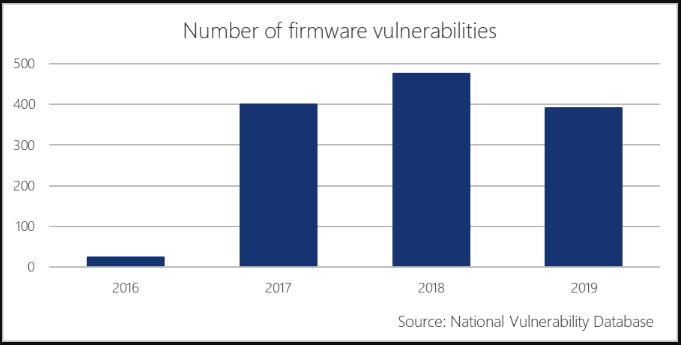
Here is a report from the National Vulnerability Database that shows firmware attacks shoot up from 2016. These attacks cause great potential risk for some industries like government, financial services and works for highly-sensitive IP.
What you should know about the Secured-core PC
The primary component of the Secured-core initiative is System Guard Secure Launch. It is a device requirement that prevents your PC’s boot process from firmware attacks. Microsoft gives a full explanation of how the device works. Here is the summary form a spokesman in the company.
System Guard uses the Dynamic Root of Trust for Measurement (DRTM) capabilities that are built into the latest silicon from AMD, Intel, and Qualcomm to enable the system to leverage firmware to start the hardware and then shortly after re-initialize the system into a trusted state by using the OS boot loader and processor capabilities to send the system down a well-known and verifiable code path.
The Secure Launch acts as a gatekeeper between actual Windows 10 operations and system start-ups (the BIOS or UEFI initialization). The Secured-core PC provides the power of newer CPUs, which can ensure everything runs smoothly as planned and prevent malicious code from latching itself onto your system before log-in.
On the official Secured-core PC web page, Microsoft announces 3 supported laptops as follow:
- Lenovo ThinkPad X1 Yoga (4th-gen)
- ThinkPad X1 Carbon (7th-gen)
- Panasonic Toughbook 55
About the Built-in Protection Layers of “Secured-core PC”
To protect against firmware attacks, Microsoft introduces 3 layers of protection for Secure-core PC. They are:
- Basic integrity protection: Secure boot, TPM 2.0, BitLocker.
- Protection form Kernel attacks: Virtualization Based Security (VBS), Hypervisor protected Code Integrity (HVCI), Kernel DMA protection.
- Protection from firmware attacks: System Guard Secure Launch, System Guard SMM protections.
In addition, the following built-in requirements allow the secured-core PC defense boot securely and protect against firmware attacks.
- Loading Windows securely: It is enabled with Hypervisors Enforced Integrity that can be used to start executables signed by approved authorities.
- Firmware Protection: System Guard Secure Launch enables the CPU to boot the device securely, which can prevent advanced firmware attacks.
- Identity Protection: You can sign in Windows Hello without a password. Credential Guard leverages VBS can prevent identity attacks.
- Secure, hardware-isolated operating environment: You can use a trusted platform like Module 2.0 and a modern CPU with the dynamic root of trust measurement (DRTM) to boot up your PC securely and minimizes firmware threats.

User Comments :